Backup / Restore the Registry
To Backup/Restore the Windows Registry: Windows 9x For XP 2000 click here
- If you are in MSDOS, at the C:\Windows prompt type
- Attrib -s -r -h C:\Windows\System.dat (press Enter)
- Attrib -s -r -h C:\Windows\User.dat (press Enter)
To make the backup copies type:
- copy C:\Windows\System.dat C:\Windows\System.000 (press Enter)
- copy C:\Windows\User.dat C:\Windows\user.000 (press Enter)
To Restore the Registry
- copy C:\Windows\System.000 C:\Windows\System.dat (press Enter)
- copy C:\Windows\User.000 C:\Windows\user.dat (press Enter)
Add Open With to all files
You can add "Open With..." to the Right click context menu of all files.This is great for when you have several programs you want to open the same file types with. I use three different text editors so I added it to the ".txt" key.
1. Open RegEdit
2. Go to HKEY_CLASSES_ROOT\*\Shell
3. Add a new Key named "OpenWith" by right clicking the "Shell" Key and selecting new
4. Set the (Default) to "Op&en With..."
5. Add a new Key named "Command" by right clicking the "OpenWith" Key and selecting new
6. Set the (Default) to "C:\Windows\rundll32.exe shell32.dll,OpenAs_RunDLL %1", C:\ being your Windows drive. You must enter the "OpenAs_RunDLL %1" exactly this way.
Customize the System Tray
You can add your name or anything you like that consists of 8 characters or less. This will replace the AM or PM next to the system time. But you can corrupt some trial licenses of software that you may have downloaded.
1. Open RegEdit
2. Go to HKEY_CURRENT_USER\Control Panel\International
3. Add two new String values, "s1159" and "s2359"
4. Right click the new value name and modify. Enter anything you like up to 8 characters.
If you enter two different values when modifying, you can have the system tray display the two different values in the AM and PM.
Lock Out Unwanted Users
Want to keep people from accessing Windows, even as the default user? If you do not have a domain do not attempt this.
1. Open RegEdit
2. Go to HKEY_LOCAL_MACHINE\Network\Logon
3. Create a dword value "MustBeValidated"
4. Set the value to 1
This forced logon can be bypassed in Safe Mode on Windows 9x
Disable the Outlook Express Splash Screen
You can make OutLook Express load quicker by disabling the splash screen:
1. Open RegEdit
2. Go to HKEY_CURRENT_USER\Software\Microsoft\OutLook Express
3. Add a string value "NoSplash"
4. Set the value data to 1 as a Dword value
Multiple Columns For the Start Menu
To make Windows use multiple Start Menu Columns instead of a single scrolling column, like Windows 9x had, Also if you are using Classic Mode in XP
1. Open RegEdit
2. Go to the key
HKEY_LOCAL_MACHINE\ Software\ Microsoft\ Windows\ CurrentVersion\ Explorer\ Advanced
3. Create a string value "StartMenuScrollPrograms"
4. Right click the new string value and select modify
5. Set the value to "FALSE"
Changing Windows' Icons
You can change the Icons Windows uses for folders, the Start Menu, opened and closed folder in the Explorer, and many more.
1. Open RegEdit
2. Go to
HKEY_LOCAL_MACHINE\ Software\ Microsoft\ Windows\ CurrentVersion\ Explorer\ Shell Icons
3. Add a string value for each Icon you wish to change.
Example: "3" ="C:\Windows\Icons\MyIcon.ico,0" This will change the closed folders in the Explorer to "MyIcon.ico". Here is a complete list for each value.
0= Unknown file type
1= MSN file types
2= Applications Generic
3= Closed Folder
4= Open Folder
5= 5.25" Drive
6= 3.25" Drive
7= Removable Drive
8= Hard Drive
9= NetWork Drive
10= Network Drive Offline
11= CD-ROM Drive
12= RAM Drive
13= Entire Network | 14= Network Hub
15= My Computer
16= Printer
17= Network Neighborhood
18= Network Workgroup
19= Start Menu's Program Folders
20= Start Menu's Documents
21= Start Menu's Setting
22= Start Menu's Find
23= Start Menu's Help
24= Start Menu's Run
25= Start Menu's Suspend
26= Start Menu's PC Undock
27= Start Menu's Shutdown | 28= Shared
29= Shortcut Arrow
30= (Unknown Overlay)
31= Recycle Bin Empty
32= Recycle Bin Full
33= Dial-up Network
34= DeskTop
35= Control Panel
36= Start Menu's Programs
37= Printer Folder
38= Fonts Folder
39= Taskbar Icon
40= Audio CD |
You need to reboot after making changes. You may need to delete the hidden file ShellIconCache if after rebooting the desired Icons are not displayed.
Change Default Folder Locations
You can change or delete the Windows mandatory locations of folder like My Documents:
1. Open RegEdit
2. Go to HKEY_CURRENT_USER\ Software\ Microsoft\ Windows\ CurrentVersion\ Explorer\ Shell Folders
3. Change the desired folder location, My Documents is normally list as "Personal"
4. Open the Explorer and rename or create the folder you wish.
To change the desired location of the Program Files folder
1. Go to
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion
2. Change the value of "ProgramFiles", or "ProgramFilesDir"
Now when you install a new program it will default to the new location you have selected.
Change the Registered Change the User Information
You can change the Registered Owner or Registered Organization to anything you want even after Windows is installed.
1) Open RegEdit
2) Got to
HKEY_LOCAL_MACHINE\ SOFTWARE\ Microsoft\ Windows\ CurrentVersion.
3) Change the value of "RegisteredOrganization" or "RegisteredOwner", to what ever you want
Opening a DOS Window to either the Drive or Directory in Explorer
Add the following Registry Keys for a Directory:
HKEY_CLASSES_ROOT\Directory\shell\opennew
@="Dos Prompt in that Directory"
HKEY_CLASSES_ROOT\Directory\shell\opennew\command
@="command.com /k cd %1"
Add or Edit the following Registry Keys for a Drive:
HKEY_CLASSES_ROOT\Drive\shell\opennew
@="Dos Prompt in that Drive"
HKEY_CLASSES_ROOT\Drive\shell\opennew\command
@="command.com /k cd %1"
These will allow you to right click on either the drive or the directory and the option of starting the dos prompt will pop up.
Changing Exchange/Outlook Mailbox Location
To change the location of your mailbox for Exchange:
1. Open RegEdit
2. Go to
HKEY_CURRENT_USER\Software\ Microsoft\Windows Messaging Subsystem\ Profiles
3. Go to the profile you want to change
4. Go to the value name that has the file location for your mailbox (*.PST) file
5. Make the change to file location or name
To change the location of your mailbox for Outlook
1. Open RegEdit
2. Go to HKEY_CURRENT_USER\Software\Microsoft\Outlook (or Outlook Express if Outlook Express)
3. Go to the section "Store Root"
4. Make the change to file location
Add/Remove Sound Events from Control Panel
You can Add and delete sounds events in the Control Panel. In order to do that:
1. Open RegEdit
2. Go to HKEY_CURRENT_USER\AppEvents\Schemes\Apps and HKEY_CURRENT_USER\AppEvents\Schemes\Eventlabels. If this key does not exist you can create it and add events.
3. You can add/delete any items you want to or delete the ones you no longer want.
Adding an Application to the Right Click on Every Folder
Here is how to add any application to the Context Menu when you right click on any Folder. This way you do not have to always go to the Start Menu. When you right click on any folder, you can have access to that application, the same as using Sent To.
1. Open RegEdit
2. Go to HKEY_CLASSES_ROOT\Folder\shell
3. Add a new Key to the "Shell" Key and name it anything you like.
4. Give it a default value that will appear when you right click a folder, i.e. NewKey (use an "&" without the quotes, in front of any character and it will allow you to use the keyboard)
5. Click on the Key HKEY_CLASSES_ROOT\Folder\shell\NewKey
6. Add a New Key named Command
7. Set the (Default) value of the application you want to run
8. For example: c:\program files\internet explorer\iexplore.exe (Include the full path and parameters if you need them)
Adding Explore From Here to Every Folder
When you want to right click on any folder and want to open up an Explorer window of that folder.
1. Open RegEdit
2. Go to HKEY_CLASSES_ROOT\Folder\shell
3. Add a new Key "RootExplore " under the "Shell" Key
4. Set the (Default) value to "E&xplore From Here "
5. Right Click the "RootExplore " Key and add a new Key "Command"to the RootExplore
6. Set the (Default) value of Explorer.exe /e,/root,/idlist,%i
Changing the Location of Windows' Installation Files
If you need to change the drive and or path where Windows looks for its installation files:
1.Open RegEdit
2.Go to
HKEY_LOCAL_MACHINE\SOFTWARE\ Microsoft\ Windows\ CurrentVersion\ Setup
3.Edit the value next to SourcePath
Creating a Logon Banner
If you want to create a Logon Banner: A message box to appear below your logon on.
1.Open RegEdit
2.Go To
For Windows 9x and ME -
HKEY_LOCAL_MACHINE\SOFTWARE\ Microsoft\ Windows\ CurrentVersion\ Winlogon
For Windows 2000 XP 2003 Vista -
HKEY_LOCAL_MACHINE\SOFTWARE\ Microsoft\ Windows\ CurrentVersion\ Winlogon
3.Create a new String value"LegalNoticeCaption "
4. Enter the Title of the window. What is displayed in the Title Bar.
5. Create a new string value "LegalNoticeText"
6. Enter the text for your message box that will appear even before the Logon window.
Creating a Default File Opener
If you have a un-registered file type and want to view it instead of having to select Open With. Use Explorer's Right-click and add your program to the right-click options by:
1. Open RegEdit
2. Go to HKEY_CLASSES_ROOT\Unknown\Shell
3. Right click on "Shell" and create a New Key and name it "Open "
4. Create a New Key under the "Open" key you just created and name it "Command"
5. Set the (Default) value to the path and filename of the program you want to use to open the file type
6. For example: C:\Windows\NOTEPAD.EXE %1
You must use the "%1" for this to work.and a space between the exe and the %1
Deleting Registry Keys from the Command Line
There are two ways to delete a key from the Registry from the Command line. At the Windows Command line:
RegEdit /l location of System.dat /R location of User.dat /D Registry key to delete
You cannot be in Windows at the time you use this switch.
Or you can create a reg file as such:
REGEDIT4
[-HKEY_LOCAL_MACHINE\the key you want to delete]
Note the negative sign just behind the[
Then at the Command line type:
1. RegEdit C:\Windows\(name of the regfile).
Change/Add Restrictions And Features
If you want to make restrictions to what users can do or use on their computer without having to run Poledit, you can edit the Registry. You can add and delete Windows features in this Key shown below.
Zero is Off and the value 1 is On. Example: to Save Windows settings add or modify the value name NoSaveSettings to 0, if set to1 Windows will not save settings. And NoDeletePrinter set to 1 will prevent the user from deleting a printer.
The same key shows up at:
HKEY_USERS\(yourprofilename)\ Software\ Microsoft\ Windows\ CurrentVersion\ Policies\ Explorer so change it there also if you are using different profiles.
1.Open RegEdit
2.Go to
HKEY_CURRENT_USER\Software\Microsoft\ CurrentVersion\ Policies
3.Go to the Explorer Key (Additional keys that can be created under Policies are System, Explorer, Network and WinOldApp )
4.You can then add DWORD or binary values set to 1 in the appropriate keys for ON and 0 for off.
NoDeletePrinter - Disables Deletion of Printers
NoAddPrinter - Disables Addition of Printers
NoRun - Disables Run Command
NoSetFolders - Removes Folders from Settings on Start Menu
NoSetTaskbar - Removes Taskbar from Settings on Start Menu
NoFind - Removes the Find Command
NoDrives - Hides Drives in My Computers
NoNetHood - Hides the Network Neighborhood
NoDesktop - Hides all icons on the Desktop
NoClose - Disables Shutdown
NoSaveSettings - Don't save settings on exit
DisableRegistryTools - Disable Registry Editing Tools
NoRecentDocsMenu - Hides the Documents shortcut at the Start button
NoRecentDocsHistory- Clears history of Documents
NoFileMenu _ Hides the Files Menu in Explorer
NoActiveDesktop - No Active Desktop
NoActiveDesktopChanges- No changes allowed
NoInternetIcon - No Internet Explorer Icon on the Desktop
NoFavoritesMenu - Hides the Favorites menu
NoChangeStartMenu _ Disables changes to the Start Menu
NoFolderOptions _ Hides the Folder Options in the Explorer
ClearRecentDocsOnExit - Empty the recent Docs folder on reboot
NoLogoff - Hides the Log Off .... in the Start Menu
And here are a few more you can play with
ShowInfoTip
NoTrayContextMenu
NoStartMenuSubFolders
NoWindowsUpdate
NoViewContextMenu
EnforceShellExtensionSecurity
LinkResolveIgnoreLinkInfo
NoDriveTypeAutoRun
NoStartBanner
NoSetActiveDesktop
EditLevel
NoNetConnectDisconnect
RestrictRun - Disables all exe programs except those listed in the RestrictRun subkey
This key has many other available keys, there is one to even hide the taskbar, one to hide the control panel and more. I'm not telling you how, as someone may want to play a trick on you. The policies key has a great deal of control over how and what program can run and how one can access what feature.
In the System key you can enter:
NoDispCPL - Disable Display Control Panel
NoDispBackgroundPage - Hide Background Page
NoDispScrSavPage - Hide Screen Saver Page
NoDispAppearancePage - Hide Appearance Page
NoDispSettingsPage - Hide Settings Page
NoSecCPL - Disable Password Control Panel
NoPwdPage - Hide Password Change Page
NoAdminPage - Hide Remote Administration Page
NoProfilePage - Hide User Profiles Page
NoDevMgrPage - Hide Device Manager Page
NoConfigPage - Hide Hardware Profiles Page
NoFileSysPage - Hide File System Button
NoVirtMemPage - Hide Virtual Memory Button
In the Network key you can enter:
NoNetSetup - Disable the Network Control Panel
NoNetSetupIDPage - Hide Identification Page
NoNetSetupSecurityPage - Hide Access Control Page
NoFileSharingControl - Disable File Sharing Controls
NoPrintSharing - Disable Print Sharing Controls
In the WinOldApp key you can enter:
Disabled - Disable MS-DOS Prompt
NoRealMode - Disables Single-Mode MS-DOS
Automatic Screen Refresh
When you make changes to your file system and use Explorer, the changes are not usually displayed until you press the F5 key
To refresh automatically:
1. Open RegEdit
2. Go to
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Update
3. Set the value name "UpdateMode" to 1
Disable Password Caching
To disable password caching, which allows for the single Network login and eliminates the secondary Windows logon screen. Either use the same password or:
1. Open RegEdit
2. Go to the key
HKEY_LOCAL_MACHINE\SOFTWARE \Microsoft\ Windows\ CurrentVersion\ Policies\ Network
3. Add a Dword value "DisablePwdCaching" and set the value to 1
Changing the MaxMTU for faster Downloads
There are four Internet settings that can be configured, you can get greater throughput (faster Internet downloads) by modifying a few settings.
They are the MaxMTU, MaxMSS and DefaultRcvWindow, and DefaultTTL
1.Open RegEdit
2.Go to
HKEY_LOCAL_MACHINE\System\CurrentControlset\ Services\ Class\ net\ 000x
(where x is your particular network adapter binding.)
3.Right click on the right panel
4.Select New\String Value and create the value name IPMTU
5.Double click on it and enter then the number you want. The usual change is to 576
6.Similarly, you can add IPMSS and give it a value of 536
(Windows 9X)You can set DefaultRcvWindow, and DefaultTTL by adding these string values to HKEY_LOCAL_MACHINE\ System\ CurrentControlset\ Services\ VXD\ MSTCP
Set the DefaultRcvWindow to"5840"and the DefaultTTL to "128"
Note: These settings will slow down your network access speed slightly, but you will probably not even see the difference if you are using a network card. If you are using Direct Cable you should see a sight difference.
Adding Items to the Start Button
To add items when you right-click on the Start Button:
1.Open RegEdit
2.Go to HKEY_CLASSES_ROOT\Directory\Shell
3.Right-click on Shell and select New Key
4.Type in the name of the key and press the Enter key
5.In the Default name that shows in the right hand panel, you can add a title with a "&" character in front of the letter for a shortcut
6.Right-click on the key you just created and create another key under it called command
7.For the value of this command, enter the full path and program you want to execute
8.Now when you right click on the Start Button, your new program will be there.
9.For example, if you want Word to be added, you would add that as the first key, the default in the right panel would be &Word so when you right click on the Start Button, the W would be the Hot Key on your keyboard. The value of the key would be C:\Program Files\Office\Winword\Winword.exe
Remove Open, Explore & Find from Start Button
When you right click on the Start Button, you can select Open, Explore or Find.
Open shows your Programs folder. Explore starts the Explorer and allows access to all drives.
Find allows you to search and then run programs. In certain situations you might want to disable this feature.
To remove them:
1.Open RegEdit
2.Go to HKEY_CLASSES_ROOT\Directory\Shell\Find
3.Delete Find
4.Scroll down below Directory to Folder
5.Expand this section under shell
6.Delete Explore and Open
Caution: - When you remove Open, you cannot open any folders.
Removing Items from NEW Context Menu
When you right-click on the desktop and select New, or use the File Menu item in the Explore and select New a list of default templates you can open up are listed.
To remove items from that list:
1. Open RegEdit
2. Do a Search for the string ShellNew in the HKEY_CLASSES_ROOT Hive
3. Delete the ShellNew command key for the items you want to remove.
Changing Telnet Window
You can view more data if you increase the line count of Telnet. By Default it has a window size of 25 lines. To increase this so you can scroll back and look at a larger number on lines:
1. Open RegEdit
2. Go to HKEY_CURRENT_USER\Software\Microsoft\Telnet
3. Modify the value data of "Rows"
Changing the Tips of the Day
You can edit the Tips of the day in the Registry by going to:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ Windows\ CurrentVersion\ explorer\ Tips
Disabling Drives in My Computer
To turn off the display of local or networked drives when you click on My Computer:
1.Open RegEdit
2.Go to
HKEY_CURRENT_USER\Software\ Microsoft\ Windows\ CurrentVersion\ Policies\ Explorer
3.Add a New DWORD item and name it NoDrives
4.Give it a value of 3FFFFFF
5.Now when you click on My Computer, none of your drives will show.
Changing the caption on the Title Bar
Change the Caption on the Title Bar for OutLook Express or the Internet Explorer:
For Outlook Express:
1. Open RegEdit
2. Go to
HKEY_CURRENT_USER\Software\Microsoft\OutLook Express
For IE5 and up use:
HKEY_CURRENT_USER\IDENTITIES \{9DDDACCO-38F2-11D6-93CA-812B1F3493B}\ SOFTWARE\ MICROSOFT\ OUTLOOK EXPRESS\5.0
3. Add a string value "WindowTitle" (no space)
4. Modify the value to what ever you like.
For no splash screen, add a dword value "NoSplash" set to 1
The Key {9DDDACCO-38F2-11D6-93CA-812B1F3493B} can be any key you find here. Each user has his own Key number.
The Key 5.0 is whatever version of IE you have
For Internet Explorer:
1. Open RegEdit
2. Go to HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Main
3. Add a string value "Window Title" (use a space)
4. Modify the value to what ever you like.
Disabling the Right-Click on the Start Button
Normally, when you right button click on the Start button, it allows you to open your programs folder, the Explorer and run Find.
In situations where you don't want to allow users to be able to do this in order to secure your computer.
1.Open RegEdit
2.Search for Desktop
3.This should bring you to HKEY_CLASSES_ROOT\Directory
4.Expand this section
5.Under Shell is Find
6.Delete Find
7.Move down a little in the Registry to Folder
8.Expand this section and remove Explore and Open
Now when you right click on the Start button, nothing should happen.
You can delete only those items that you need.
Note: - On Microsoft keyboards, this also disables the Window-E (for Explorer) and Window-F
(for Find) keys.
See the section on Installation in the RESKIT to see how to do this automatically during an install.
Disabling My Computer
In areas where you are trying to restrict what users can do on the computer, it might be beneficial to disable the ability to click on My Computer and have access to the drives, control panel etc.
To disable this:
1.Open RegEdit
2.Search for 20D04FE0-3AEA-1069-A2D8-08002B30309D
3.This should bring you to the HKEY_CLASSES_ROOT\CLSID section
4.Delete the entire section.
Now when you click on My Computer, nothing will happen.
You might want to export this section to a Registry file before deleting it just in case you want to enable it again. Or you can rename it to 20D0HideMyComputer4FE0-3AEA-1069-A2D8-08002B30309D. You can also hide all the Desktop Icons, see Change/Add restrictions.
Opening Explorer from My Computer
By default, when you click on the My Computer icon, you get a display of all your drives, the Control Panel etc. If you would like to have this open the Explorer:
1. Open RegEdit
2. Go to
HKEY_CLASSES_ROOT\CLSID\ {20D04FE0-3AEA-1069-A2D8-08002B30309D}\ Shell
3 . Add a new Key named "Open" if it does not exists by right clicking "Shell" and selecting new.
4. . Add a new Key named "Command" by right clicking "Open" and selecting new
5. Set the (Default) value for the Command Key to "Explorer.exe" or "C:\Windows\Explorer.exe"
Recycle Bin Edits
Fooling with the recycle bin. Why not make the icon context menu act like other icon context menus.
Add rename to the menu:
HKEY_CLASSES_ROOT\CLSID\ {645FF040-5081-101B-9F08-00AA002F954E}\ ShellFolder
"Attributes"=hex:50,01,00,20
Add delete to the menu:
HKEY_CLASSES_ROOT\CLSID\ {645FF040-5081-101B-9F08-00AA002F954E}\ ShellFolder
"Attributes"=hex:60,01,00,20
Add rename and delete to the menu:
HKEY_CLASSES_ROOT\CLSID\ {645FF040-5081-101B-9F08-00AA002F954E} \ShellFolder
"Attributes"=hex:70,01,00,20
Restore the recycle bin to Windows defaults including un-deleting the icon after deletion:
Restore the icon.
HKEY_LOCAL_MACHINE\SOFTWARE\ Microsoft\ Windows \CurrentVersion\ explorer\
Desktop\NameSpace\{645FF040-5081-101B-9F08-00AA002F954E}
@="Recycle Bin"
Reset Windows defaults.
HKEY_CLASSES_ROOT\CLSID\ {645FF040-5081-101B-9F08-00AA002F954E} \ShellFolder
"Attributes"=hex:40,01,00,20
Other edits to the recycle bin icon:
HKEY_CLASSES_ROOT\CLSID\ {645FF040-5081-101B-9F08-00AA002F954E}\ ShellFolder
"Attributes"=hex:40,01,01,20 ... standard shortcut arrow
"Attributes"=hex:40,01,02,20 ... a different shortcut arrow
"Attributes"=hex:40,01,04,20 ... and still another shortcut arrow
"Attributes"=hex:40,01,08,20 ... make it look disabled (like it's been cut)
For Windows XP and 2000 also edit HKEY_CURRENT_USER\ Software\ Microsoft\ Windows\ CurrentVersion\ Explorer\ CLSID\ {645FF040-5081-101B-9F08-00AA002F954E}
For Windows ME also edit HKEY_CURRENT_USER \Software\ Classes\ CLSID\ {645FF040-5081-101B-9F08-00AA002F954E}
Setting the Minimum Password Length
1.Open RegEdit
2.Go to
HKEY_LOCAL_MACHINE\ SOFTWARE\ Microsoft\ Windows\ CurrentVersion\ Policies\ Network
3. Now, choose the Edit/New/Binary value command and call the new value MinPwdLen. Press Enter twice and Assign it a value equal to your minimum password length.
Add\delete programs to run every time Windows starts
You can start or stop programs from executing at boot up by adding or deleting them to/from the run Keys in the Registry. Windows loads programs to start in the following order; Program listed in the Local Machine hive, then the Current User hive, then theWin.ini Run= and Load = lines. then finally programs in your Start Up folder.
To add or remove programs in the Registry
1.Open RegEdit
2.Go to the desired Key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows \CurrentVersion \Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows \CurrentVersion \RunServices
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows \CurrentVersion \Run
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows \CurrentVersion \RunServices
3. Add a new String Value and name it anything you like
4. For the value data, enter the path and executable for the program you want to run.
By adding the value to the HKEY_CURRENT_USER hive instead allows the program to start only when that user is logged on.
If you add the value to the RunOnce key the program will run once and be removed from the key by Windows.
Removing the Shortcut Icon Arrows
1.Open RegEdit
2.Open the Key HKEY_CLASSES_ROOT
3.Open the Key LNKFILE
4.Delete the value IsShortcut
5.Open the next Key PIFFILE
6.Delete the value IsShortcut
7.Restart the Windows
Turn Off Window Animation
You can shut off the animation displayed when you minimize and maximize Windows.
1. Open RegEdit
2. Go to HKEY_CURRENT_USER\Control panel \Desktop\ WindowMetrics
3. Create a new string value "MinAnimate".
4. Set the value data of 0 for Off or 1 for On
Changing your Modem's Initialization String
1.Open RegEdit
2.Go to
HKEY_LOCAL_MACHINE\System\CurrentControlSet \Services \Class \Modem \0000 \Init
3.Change the settings to the new values
Increasing the Modem Timeout
If your modem it is timing out during file transfers or loading Web Pages, you might try increasing the timeout period. To change the Time Out::
1.Open RegEdit
2.Go to HKEY_LOCAL_MACHINE\System\CurrentControlSet\ Services\ Class\ Modem\ XXXX\ Settings Where XXXX is the number of your modem
3. In the right panel and double click on Inactivity Timeout
4.The number of minutes for a timeout should be entered between the brackets.
5.For example, a setting could have S19=<10> to set it to 10 minutes.
Removing Programs from Control Panel's Add/Remove Programs Section
If you uninstalled a program by deleting the files, it may still show up in the Add/Remove programs list in the Control Panel.
In order to remove it from the list.
1.Open RegEdit
2.Go to HKEY_LOCAL_MACHINE\ SOFTWARE\ Microsoft\ Windows\ CurrentVersion\ Uninstall
3.Delete any programs here.
If you have a problem locating the desired program open each key and view the DisplayName value
The Fix for Grayed Out Boxes
The File Types tab in Explorer's View / Options menu lets you edit most of your file types, but certain settings cannot be changed. The default action for a batch file, for instance, runs the batch file instead of opening it via Notepad or Wordpad. Thus, when you double-click on AUTOEXEC.BAT, a DOS window opens, and the file executes. If you want to change this default action and edit a batch file when you double-click on it, however, the File Types tab does not let you do so; the Set Default button for the file type called MS-DOS Batch File is always grayed out.
The button is grayed out because HKEY_CLASSES_ROOT's batfile key contains an EditFlag value entry. Such entries are used throughout the Registry to prevent novice users from altering certain system settings. The binary data in batfile's EditFlag reads d0 04 00 00. If you change this value to 00 00 00 00, you can then change any of the batch file settings. Do not, however, indiscriminately zero out EditFlag; if you do so in a system ProgID such as Drive or AudioCD, it completely disappears from the File Types list. For ProgIDs that are linked to extensions, set all EditFlags to 00 00 00 00. For system ProgIDs, replace EditFlag data with 02 00 00 00.
If you wish to have access to some buttons while leaving others grayed out, you must know the function of each EditFlag bit. The last two bytes of data are always zero, but most bits within the first two bytes have a specific effect:
- Byte 1, bit 1: Removes the file type from the master list in the File Types tab (select View / Options under Explorer) if it has an associated extension.
- Byte 1, bit 2: Adds the file type to the File Types tab if it does not have an associated extension.
- Byte 1, bit 3: Identifies a type with no associated extension.
- Byte 1, bit 4: Grays out the Edit button in the File Types tab.
- Byte 1, bit 5: Grays out the Remove button in the File Types tab.
- Byte 1, bit 6: Grays out the New button in the Edit File Type dialog (select the Edit button in the File Types tab).
- Byte 1, bit 7: Grays out the Edit button in the Edit File Type dialog.
- Byte 1, bit 8: Grays out the Remove button in the Edit File Type dialog.
- Byte 2, bit 1: Prevents you from editing a file type's description in the Edit File Type dialog.
- Byte 2, bit 2: Grays out the Change Icon button in the Edit File Type dialog.
- Byte 2, bit 3: Grays out the SetDefault button in the Edit File Type dialog.
- Byte 2, bit 4: Prevents you from editing an action's description in the Edit Action dialog (select the Edit button in the Edit File Type dialog).
- Byte 2, bit 5: Prevents you from editing the command line in the Edit Action dialog.
- Byte 2, bit 6: Prevents you from setting DDE (Dynamic Data Exchange) fields in the Edit Action dialog.
The EditFlags value for Drive, for instance, is d2 01 00 00 in Hex (1101 0010 0000 0001 in binary). Bits 2, 5, 7, and 8 are on in byte 1, and bit 1 is on in byte 2. The EditFlag for batfile is d0 04 00 00 in Hex or 1101 0000 0000 0100 in binary. In this case, bits 5, 7, and 8 are on in byte 1, and bit 3 is on in byte 2.
Bits 4, 5, and 6 of byte 2 apply only to actions that are protected. EditFlags with action keys (such as HKEY_CLASSES_ROOT\batfile\shell\open) determine protection. If byte 1, bit 1 of such an EditFlag is 0 (or if there is no EditFlag), then the action is protected. If byte 1, bit 1 is 1, then the action is unprotected.
Protection on system files
To enable protection on system files such as the KnownDLLs list, add the following value;
1. Open RegEdit
2. HKEY_LOCAL_MACHINE\System\CurrentControlSet\ Control\ SessionManager
3. Create the a Dword value and name it "ProtectionMode "
4. Set the Value to1
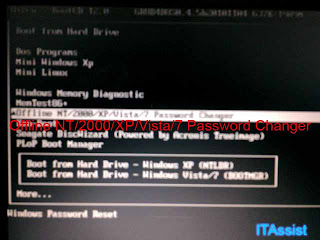 In our case, here is the menu we ended up having after we bootup. What we are looking for here is Offline NT/2000/XP/VISTA/7 Password changer. It is visible in the image as white highlighted texts.
In our case, here is the menu we ended up having after we bootup. What we are looking for here is Offline NT/2000/XP/VISTA/7 Password changer. It is visible in the image as white highlighted texts.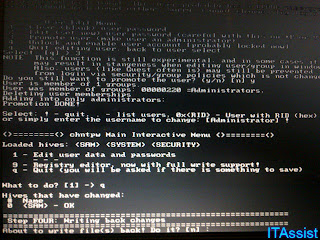 After some analyzing, we ended up loading the SAMs and security hives. The screen shows 3 accounts, 1. Administrator, 2. Guest 3. xxxx in my case.
After some analyzing, we ended up loading the SAMs and security hives. The screen shows 3 accounts, 1. Administrator, 2. Guest 3. xxxx in my case.