First things first, the exercise must be practiced in an authorized environment and is written with intention to make aware to System Admins, Support staff, IT technicians, Computer students who wish to solve problems of forgotten passwords or broaden knowledge. We cannot be held responsible for any trouble cause if taken irresponsibly.
Real Subject is: Passwords in Windows 7 can be reset easily with Hirens BootCD 12.
In our test, we download Hirens BootCD 12 (HBCD) from a mirror site link from www.9down.com page where the HBCD release story was published. As we read, the download link might be removed because some hosts consider as violation to their terms of services.
Anyways, the links to where we got HBCD 12 iso are posted above.
Burn the ISO and boot the CD. It's only a CD of not more than 400MB of codes of different useful admin programs. So 400MB is not much, you could download it over night in a decent ADSL connection in the Pacific Islands.
There are 4 Steps, but will try to make brief guide on what I can remember.
After burning the Image copy of Hirens BootCD 12 to a blank CD, guide the laptop/PC to boot from CD/DVD mode.
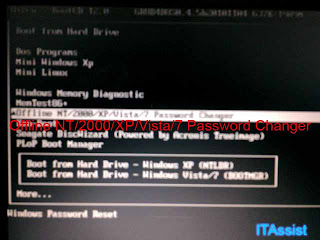 In our case, here is the menu we ended up having after we bootup. What we are looking for here is Offline NT/2000/XP/VISTA/7 Password changer. It is visible in the image as white highlighted texts.
In our case, here is the menu we ended up having after we bootup. What we are looking for here is Offline NT/2000/XP/VISTA/7 Password changer. It is visible in the image as white highlighted texts.The next steps were basically Enter to continue and Enter for default values. Note that it will specifically ask for drives to mount, just select to mount drives that makes sense to be the c: drive on the laptop/PC. In laptops you will expect to see /sda's and desktop pc's as /hda (I'm not sure), but also you can differentiate between drives too by reading the size.
Where to locate the registry, just hit enter. It works in my case (system32). I'm sure it search the sub folders in system32 :).
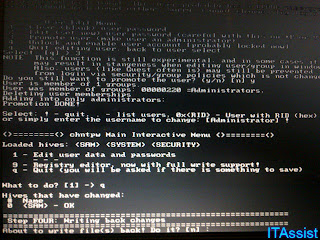 After some analyzing, we ended up loading the SAMs and security hives. The screen shows 3 accounts, 1. Administrator, 2. Guest 3. xxxx in my case.
After some analyzing, we ended up loading the SAMs and security hives. The screen shows 3 accounts, 1. Administrator, 2. Guest 3. xxxx in my case.Note that Windows 7 Administrator accounts are locked by default in every distribution. Do not attempt to reset the password for Admins only and leave. Wishful thinking if you are attempting to penetrate without altering the other users passwords but you might find yourself trying to login as Admin. So make sure you unlock/enable the Admin account too (option3). Guest is always ignored for login, so do not bother.
Also you will realize the Selection option need to use numbers or letters listed. Do not be confused with the final process to quit and update the SAM's database that you have altered. Without knowing how to properly quit, you could run away not saving the changes or stuck in a loop of options.
The symbol ! or exclamation mark (!) is the quit symbol to saving the SAMs and you can power off or alt+ctrl+del to reboot the machine to windows 7 environment to try login.
Select: ! - quit
Do not type q or quit or you will open a loop :)
There are other options to explore which could be useful for different interests.
Have fun! ITA Team







No comments:
Post a Comment