| Step 1 Step 2 Step 3 Step 4 Step 5 Step 6 |
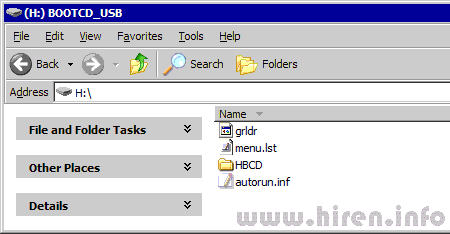
Hiren's BootCD From USB Flash Drive (Pen Drive) - www.hiren.info
Affidavit Details FBI "Operation Payback" Probe | The Smoking Gun
DECEMBER 29--As part of an international criminal probe into computer attacks launched this month against perceived corporate enemies of WikiLeaks, the FBI has raided a Texas business and seized a computer server that investigators believe was used to launch a massive electronic attack on PayPal, The Smoking Gun has learned.
 The FBI investigation began earlier this month after PayPal officials contacted agents and “reported that an Internet activist group using the names ‘4chan’ and “Anonymous” appeared to be organizing a distributed denial of service (“DDoS”) attack against the company,” according to an FBI affidavit excerpted here.
The FBI investigation began earlier this month after PayPal officials contacted agents and “reported that an Internet activist group using the names ‘4chan’ and “Anonymous” appeared to be organizing a distributed denial of service (“DDoS”) attack against the company,” according to an FBI affidavit excerpted here.
The PayPal assault was part of “Operation Payback,” an organized effort to attack firms that suspended or froze WikiLeaks’s accounts in the wake of the group’s publication of thousands of sensitive Department of State cables. As noted by the FBI, other targets of this “Anonymous” effort included Visa, Mastercard, Sarah Palin’s web site, and the Swedish prosecutor pursuing sex assault charges against Julian Assange, the WikiLeaks founder.
On December 9, PayPal investigators provided FBI agents with eight IP addresses that were hosting an “Anonymous” Internet Relay Chat (IRC) site that was being used to organize denial of service attacks. The unidentified administrators of this IRC “then acted as the command and control” of a botnet army of computers that was used to attack target web sites.
 Federal investigators noted that “multiple, severe DDos attacks” had been launched against PayPal, and that the company’s blog had been knocked offline for several hours. These coordinated attacks, investigators allege, amount to felony violations of a federal law covering the “unauthorized and knowing transmission of code or commands resulting in intentional damage to a protected computer system.”
Federal investigators noted that “multiple, severe DDos attacks” had been launched against PayPal, and that the company’s blog had been knocked offline for several hours. These coordinated attacks, investigators allege, amount to felony violations of a federal law covering the “unauthorized and knowing transmission of code or commands resulting in intentional damage to a protected computer system.”
The nascent FBI probe, launched from the bureau’s San Francisco field office, has targeted at least two of those IP addresses, according to the affidavit sworn by Agent Allyn Lynd.
One IP address was initially traced to Host Europe, a Germany-based Internet service provider. A search warrant executed by the German Federal Criminal Police revealed that the “server at issue” belonged to a man from Herrlisheim, France. However, an analysis of the server showed that “root-level access” to the machine “appeared to come from an administrator logging in from” another IP address.
“Log files showed that the commands to execute the DDoS on PayPal actually came from” this IP, Agent Lynd reported. Two log entries cited in the affidavit include an identical message: “Good_night,_paypal_Sweet_dreams_from_AnonOPs.”
 Investigators traced the IP address to Tailor Made Services, a Dallas firm providing “dedicated server hosting.” During a December 16 raid, agents copied two hard drives inside the targeted server. Court records do not detail what was found on those drives, nor whether the information led to a suspect or, perhaps, a continuing electronic trail. In a brief phone conversation, Lynd declined to answer questions about the ongoing denial of service probe.
Investigators traced the IP address to Tailor Made Services, a Dallas firm providing “dedicated server hosting.” During a December 16 raid, agents copied two hard drives inside the targeted server. Court records do not detail what was found on those drives, nor whether the information led to a suspect or, perhaps, a continuing electronic trail. In a brief phone conversation, Lynd declined to answer questions about the ongoing denial of service probe.
Search warrant records indicate that agents were authorized to seize records and material relating to the DDoS attacks “or other illegal activities pertaining to the organization “Anonymous” or “4chan.”
A second IP address used by “Anonymous” was traced to an Internet service provider in British Columbia, Canada. Investigators with the Royal Canadian Mounted Police determined that the Canadian firm’s “virtual” server was actually housed at Hurricane Electric, a California firm offering “colocation, web hosting, dedicated servers, and Internet connections,” according to its web site.
FBI Agent Christopher Calderon, an expert on malicious botnets who works from the bureau’s San Jose office, is leading the probe of the second IP (and presumably has seized a server from Hurricane Electric). Hurricane’s president, Mike Leber, did not respond to a message left for him at the firm’s office in Fremont, which is about 20 miles from PayPal’s San Jose headquarters. (5 pages)
'SMS of Death' and GSM Eavesdropping Revealed in Berlin - Security Watch
http://blogs.pcmag.com/securitywatch/2010/12/sms_of_death_and_gsm_eavesdrop.php
The annual Chaos Communication Congress (CCC) in Berlin has seen revelations of an 'SMS of Death' attack against many conventional non-smartphones and a toolkit for eavesdropping on calls and text messages ob any GSM network.
The SMS of Death involves a malicious SMS text message to a phone which can effectively 'brick' the phone (make it useless). The research focused not on smart phones like the iPhone, but on less sophisticated phones like the Nokia N40, the Motorola RAZR and the Samsung S5230 Star and S3250. In some cases, the attack would disconnect the phone and force it to reboot; but since the phone did not acknowledge receipt of the message, the network would continue sending it.
The attack probably isn't as scary as the name implies. Attacks like this have been found many times in the past and are always dealt with by network providers by filtering at their end. This may have already been done in the case of the SMS of Death.
The GSM attack, described in this BBC story. GSM (Global System for Mobile communications) is the most popular network architecture for mobile telephone systems, servicing an estimated 5 billion devices and dominant outside of the US. Researchers Karsten Nohl and Silvain Munaut demonstrated at the CCC a kit which can locate any GSM phone by taking its unique ID and using it to intercept data transferred between the phone and base. They decrypt this transmission using a decryption tool using a 'rainbow key'. If such a technique works, it probably indicates a fundamental weakness in GSM encryption.
Hat tip on the GSM issue to Threatpost.
Ed Roberts, developer of MITS Altair 8800 computer.
Late Ed Roberts, was an engineer who helped develop a precursor to the modern personal computer.
Roberts was best known for developing and marketing the MITS Altair 8800 in the 1970s.
The build-it-yourself kit was operated by switches and had no display screen initially, but it inspired Bill Gates and his childhood friend Paul Allen to found Microsoft in 1975 after they saw an article about the Altair in Popular Mechanics. Gates and Allen founded Microsoft in Albuquerque to be based near MITS' headquarters.
-- Associated Press
Photo: Ed Roberts poses with the Altair 8800 computer in 1997. Credit: Associated Press / Atlanta Journal Constitution, William Berry
BIOS Setup Utility Access Keys for Major BIOS Manufacturers
Every computer's motherboard has a BIOS manufacturer.
This list of BIOS access keyboard commands should get you in without problem.
As your computer boots up, look for one of the following BIOS manufacturer's names to flash on the screen. The BIOS manufacturer name usually appears as a logo in the top-left corner or as text at the very bottom of the screen.
After verifying the creator of the BIOS on your system, reference the following list and use the appropriate keyboard command to access the BIOS setup utility.
AMI (American Megatrends) - AMIBIOS, AMI BIOS
- Press Del when after powering on the computer.
- Some older motherboards that use AMIBIOS may prompt for the F1 or F2 key instead.
Award Software (now part of Phoenix Technologies) - AwardBIOS, Award BIOS
- Press the Del key to enter the BIOS Setup Utility on nearly all AwardBIOS powered motherboards.
- Some older systems using Award's BIOS software asked for Ctrl+Alt+Esc to enter BIOS.
DTK (Datatech Enterprises) - DTK BIOS
- Press the Esc key to enter BIOS, right after powering on the PC.
Microid Research - MR BIOS
- Press F1 to access the BIOS setup utility.
Phoenix Technologies - Phoenix BIOS, Phoenix-Award BIOS
- Press Del during the Power On Self Test, immediately after the computer starts.
- Many older Phoenix BIOS systems required Ctrl+Alt+Esc, Ctrl+Alt+Ins, or Ctrl+Alt+S to access BIOS.
If you're still having troubles entering BIOS or can't figure out what company supplied the BIOS on your motherboard, here are some keyboard commands you might want to randomly try in addition to the any of the ones listed above:
- F3
- F4
- F10
- F12
- Tab
- Ctrl+Alt+F3
- Ctrl+Alt+Del
- Ctrl+Alt+Shift+Del (using Del from the keypad)
- Ctrl+Insert
- Ctrl+Shift+Esc
- Fn+[any "F" function key] (on some laptops)
BGP routing: last hurdle to establish Fiji as the Internet Hub of the Pacific
---
For a long time in Fiji there were only 3 Autonomous System Number (ASN), Fintel (2941), USP(24390) and a F-Root server(3557) hosted by USP.
These ASN represent network clouds interconnected to each other. The interconnection information is exchanged via the Border Gateway Protocol (BGP). BGP tables define the backbone of the Internet: the tables hold the information on how to reach any IP address from any other IP address. BGP provides you with a complete view of the Internet, and you can choose with some capabilities the way your packets will travel from one destination to the other, but more importantly it allows you to have many paths to the rest of the Internet offering redundancy and reliability. When one BGP link is destroyed, the advertised routes are removed from the peering point and the peers of this peer and so on, which generates a reconfiguration of the Internet. If you have more than one BGP link, the other links gain higher priority and your packets are automatically rerouted via the alternate paths.
Wikipedia defines BGP as "The Border Gateway Protocol (BGP) is the protocol backing the core routing decisions on the Internet. It maintains a table of IP networks or 'prefixes' which designate network reachability among autonomous systems (AS). It is described as a path vector protocol. BGP does not use traditional Interior Gateway Protocol (IGP) metrics, but makes routing decisions based on path, network policies and/or rulesets. For this reason, it is more appropriately termed a reachability protocol rather than routing protocol."
In Fiji, the situation until recently (a month ago) is that FINTEL is connected (via the Southern Cross Cable) to the Internet backbone via BGP and is providing, static routes (non BGP) to the various ISPs (CONNECT, UNWIRED, KIDANET, VODAFONE, DIGICEL). Additionally, USP, the University of the South Pacific, with is main campus in Suva, Fiji, has its own Internet link to AARNET. USP is not connected locally to FINTEL. Internet packets from a student at home, have to go via Australia to reach an online courseware in the University, just across the road. USP also installed a Root Server on its network, this root server is only connected to USP network and therefore does not benefit any other ISP in Fiji.
A month ago, TFL, Telecom Fiji Limited (CONNECT parent company) got access to the Southern Cross Cable and set up its own link to the Internet via the ASN 45349, but as of today, FINTEL, TFL, USP are still not interconnected.
At the moment, none of these entities offer BGP peering, to any organization in Fiji. Why would you want BGP, static routes are more than enough, is the common question when asked about BGP peering in Fiji. BGP is a protocol that allows redundancy and reliability. It self configures depending on network conditions. Having more than one peering point, allows better operation, less downtime, etc... This is very important for the development of the Internet economy in Fiji, opening a wide range of operations and local content.
How can you get therefore reliability, and redundancy using BGP when no local ISPs offers you BGP Peering?
The answer is tunnels. Using the same method to get IPv6 when you local provider does not have native IPv6, you establish an IPv6 tunnel over IPv4 to a remote host. Here the trick is to create a tunnel, to make two peers look like next to each others. You then move IPv4 over IPv4. The whole tunnel is considered as a link (like a phone line, or DSL link), BGP can then run on top of this link, and provide the same capabilities as if the link was a physical link between two modems. You then use at the other end a remote router, which has BGP peering to the rest of the Internet, establish a tunnel from your office router to this router and then BGP peer with it. However you need to be careful that the route advertisement do not overwrite the route that allows the tunnel to function. Therefore on each router, you enter a static route to indicate the other end of the tunnel is not reached via the tunnel but via the local link. Because this route is more specific it will have priority over more generic routes.
It is indeed a cumbersome set up, but it has proven very reliable for our AS55327, it has also reduced drastically our downtime, and network reconfigurations each time one of our ISPs is down, making a breeze to operate a Network Operating Centre in Fiji. Until local ISPs offer BGP peering to finally fulfill the objectives of becoming the Internet hub of the Pacific, development in Internet in Fiji will be very limited. Call Centers, Data Centers, Internet Exchange points, Education (cf lack of peering with USP), local hosting, Content Delivery Network (CDN), will be very difficult to be established without this fundamental block.
In a paper at http://www.caida.org/publications/presentations/2006/wealthofnetworks/ Tom Vest, Internet Economist at CAIDA and OECD correlates the wealth of an economy to the wealth of networks and the number of ASN an economy has.
http://www.avonsys.com/blog3
Difference between RSS and Atom
RSS 2.0 has the widest acceptance of any feed format
RSS does not allow any well-formed XML markup in it's content
RSS has only three required fields on a per item basis- title, link and description
RSS requires descriptive fields such as title and link only in item breakdowns
ATOM
Atom is a relatively recent spec and is much more robust and feature-rich than RSS
Atom requires descriptive fields for both items and the full feed
Atom feeds provide an "updated" field which means that any feeds that are modified have a timestamp associated with them
Atom feeds usually contain a self pointer autodiscovery URL
more information can be obtained from Tim Bray's comparison site.
Hackers Defend WikiLeaks by Attacking PayPal and PostFinance
referred to as Anonymous, have retaliated against several sites which
have denied service to WikiLeaks shortly after the site started
leaking secret embassy cables.
The site of Swiss bank PostFinance, which has closed the account of
WikiLeaks founder Julian Assange, has been taken down and is still
unavailable at the time of this writing. Hackers have also attacked
PayPal but have only managed to take down the site's blog, while the
service remained operational.
A spokesman for the group behind the attacks on PayPal and PostFinance
said they will target any website that's "bowing down to government
pressure." The same group is allegedly behind the series of attacks
collectively called "Operation: Payback," which targeted anti-piracy
organizations such as RIAA and MPAA.
Among other companies that have denied service to WikiLeaks are DNS
service provider EveryDNS.net and Amazon. Most of these sites claim
they haven't shut down WikiLeaks' account due to political pressure,
instead naming technical or procedural reasons for denying the service
to the WikiLeaks.
WikiLeaks founder Julian Assange arrested
WikiLeaks founder arrested in London
Paola Totaro in London
December 7, 2010 - 10:47PM
WikiLeaks founder Julian Assange arrested
He is to appear in a London court shortly
Scores of photographers and journalists waiting at court
WikiLeaks tweets arrest "won't affect our operations"
The founder of WikiLeaks, Julian Assange, has been arrested by London police on behalf of Swedish authorities on suspicion of rape.
The Metropolitan Police Extradition Unit confirmed at 10.30am London time (2030 AEDT) that the 39-year-old Australian had been arrested "by appointment" on a European Arrest Warrant an hour earlier.
Members of the media gather outside the rear entrance of Westminster Magistrates Court in London. Photo: AP
The Swedish warrant cites one count of unlawful coercion, two counts of sexual molestation and one count of rape – all allegedly committed in August this year.
The Australian-born human rights lawyer, Geoffrey Robertson QC, has cut short his annual summer holiday in Sydney to represent Mr Assange.
Mr Robertson and another specialist extradition lawyer from his Doughty Street Chambers are to act for Mr Assange and appear in a magistrate's court within 24 hours to argue for bail. A full hearing of the extradition case must be heard inside 28 days.
However, London legal sources warned that the type of European arrest warrant issued against Mr Assange over sexual assault claims in Sweden was extremely difficult to "avoid or challenge". He and his lawyers planned to fight the extradition with every available resource because of growing fears that this case would allow for preparation for an immediate follow-up and handover to US authorities in the wake of the release of hundreds of thousands of US diplomatic cables.
This website understands that Mr Robertson, whose Chambers are one of the few with specialist experience in extradition proceedings with Scandinavian nations, has been in contact with Mr Assange for some time about his defence and met with federal Attorney-General Robert McClelland last week about the case.
The surrender of Mr Assange is unfolding as his whistleblower's website continued to battle a seemingly concerted global effort to combat further information release led by the US Attorney-General, Eric Holder.
Mr Holder said he had authorised "significant" actions aimed at prosecuting the WikiLeaks founder, but refused to specify what these might be.
"The lives of people who work for the American people have been put at risk. The American people themselves have been put at risk by these actions that I believe are arrogant, misguided and ultimately not helpful in any way. We are doing everything that we can."
Mr Assange is reported by The Guardian to be seeking supporters to put up surety and bail and has said he expected to have to raise between £100,000 and £200,000 – and six people offering surety – to stave off attempts to hold him in remand.
Mr Assange has reportedly told friends that he was increasingly convinced the US was behind Swedish prosecutors' attempts to extradite him for questioning on the assault allegations.
He has previously said that the original allegations were the product of "personal issues" but that he now believed Sweden had behaved as "a cipher" for the US.
Mr Assange is wanted by Swedish detectives after two women claimed they were sexually assaulted by him when he visited the country last August. The Swedish supreme court upheld an order to detain him for questioning after he successfully appealed against two lower court rulings.
Mr Assange has also said that he declined to return to Sweden to face prosecutors because he feared he would not receive a fair trial and that prosecutors had requested that he be held in solitary confinement and incommunicado.
He has admitted that he was becoming exhausted by the battle to keep defending the allegations in Sweden while running the carefully managed release of the US cables at the same time.
A Swiss bank announced this week said that had shut down Mr Assange's account because he had allegedly given "false information", while the US-based commerce business PayPal has also frozen the WikiLeaks accounts, hindering the site's ability to raise funds.
Assange has $61,000 (£38,000) in PayPal and $37,000 in the Swiss account, sources said.
American political rhetoric and attacks against WikiLeaks are escalating, with the former vice-presidential candidate Sarah Palin exploiting global debate to describe Mr Assange as "an anti-American operative with blood on his hands".
According to the veteran Republican Mike Huckabee, "anything less than execution is too kind a penalty".
However in Australia today, Prime Minister Julia Gillard backed away from her comment of late last week that the actions of Mr Assange and WikiLeaks were "illegal".
When asked what, under Australian law, was illegal about his actions, she was unable to nominate anything: "The foundation stone of it is an illegal act," Ms Gillard said.
The "foundation stone" was the initial theft of the cables - allegedly committed by a US army private - and not the publication by WikiLeaks.
"It would not happen, information would not be on WikiLeaks, if there had not been an illegal act undertaken," Ms Gillard said.
The opposition's legal affairs spokesman, Senator George Brandis, later called Ms Gillard's use of language "clumsy".
"As far as I can see he [Mr Assange] hasn't broken any Australian law, nor does it appear he has broken any American laws," he told Sky News.
Mr Assange has written an opinion piece in The Australian newspaper for Wednesday in which he refers to a young Rupert Murdoch in 1958, then owner and editor of Adelaide's The News, who said: "In the race between secrecy and truth, it seems inevitable that truth will always win".
The piece, which the paper released a snipet of before Wednesday's publication, argues the need for freedom of speech and refers to the "dark days" of corrupt government in Queensland (where Mr Assange was raised) as well as the Fitzgerald inquiry and much about his upbringing in a country town, "where people spoke their minds bluntly".
Mr Assange reportedly claims Australian politicians' chant of "You'll risk lives! You'll endanger troops!" with the US makes no sense as they argue in the same breath that "there is nothing of importance in what WikiLeaks publishes. It can't be both", he says.
Scores of photographers and journalists are waiting in zero degree cold as reports emerged that Mr Assange would appear in the Magistrate's Court in London's Horseferry road by 2pm London time (0100 AEDT).
A statement on Twitter from WikiLeaks tweeted that "today's actions against our editor-in-chief Julian Assange won't affect our operations: we will release more cables tonight as normal".
http://www.latimes.com/news/nationworld/world/la-fg-wikileaks-assange-arrest-20101208,0,10353.story
Julian Assange, the founder of the controversial WikiLeaks website, was arrested Tuesday and ordered to remain in custody until a hearing next week on his possible extradition to Sweden.
Assange, 39, turned himself in to police Tuesday morning, hours after Britain received a formal warrant for his arrest from Swedish authorities. Assange denies any wrongdoing and says he will fight the attempt to extradite him, beginning with a hearing Dec. 14.
That could be the start of a legal battle that could drag on for weeks or even months, in part because the case against him in Sweden remains rather murky. Assange, who is Australian, is eager to avoid extradition for fear that it could set the stage for him to be sent to the U.S. if prosecutors there charge him with offenses relating to the WikiLeaks disclosures of State Department diplomatic cables and classified Pentagon files related to the wars in Iraq and Afghanistan.
Those leaked files have turned Assange into an international figure, vilified by the U.S. and governments around the world for spilling official secrets but lionized by activists demanding a free flow of information. In Washington, the Obama administration blames Assange for recklessly damaging U.S. relations with other countries and even aiding terrorists.
A spokesman for WikiLeaks vowed that Assange's arrest would not affect the website's plans to continue publishing its cache of confidential documents.
The accusations against Assange in Sweden have dogged him since the summer, before his organization began releasing portions of its huge trove of rifled State Department cables. The allegations stem from separate sexual encounters he had with two women in August, which Swedish prosecutors say may have involved molestation, "unlawful coercion" and rape.
Assange insists that the liaisons were consensual. His lawyer, Mark Stephens, characterizes the case as a "dispute over consensual but unprotected sex."
Assange's supporters accuse the U.S. of pushing the case behind the scenes as a way of embarrassing, harassing and silencing him.
Tuesday's arrest came as the net around Assange and WikiLeaks continued to tighten.
Several days ago, Amazon.com booted WikiLeaks from its Internet servers, and the online pay service PayPal also severed its links with the website. On Monday, a Swiss bank froze an account Assange had opened to raise funds, and on Tuesday, Visa announced that it too was suspending its business with WikiLeaks, the Associated Press reported.
Stephens has denounced Sweden as "one of the lickspittle states" that have kowtowed to American demands in the past, particularly by assisting in the controversial practice of "extraordinary rendition" of terrorism suspects.
The lawyer also asserts that Assange has been willing from the start to cooperate with Swedish authorities in their investigation, but that his offers to submit to some form of questioning, both in Sweden while he was still in the country and later in London, were repeatedly rebuffed.
"We are in the rather exotic position of not having seen any of the evidence [of the crimes] that Mr. Assange is accused of," Stephens told reporters after Tuesday's preliminary hearing.
In a packed London courtroom Tuesday afternoon, Assange formally refused voluntary extradition to Sweden and asked to be released on bail. Throughout the hourlong hearing, Assange, in a dark suit, sat quietly in a glassed-in booth reserved for defendants.
Prosecutors objected to the bail request, saying that Assange's nomadic lifestyle made him a flight risk. They noted that he first gave the court only a post office box as an address and, when that was disallowed, a street address in Victoria state in his native Australia.
The judge sided with the prosecution, despite the presence of several high-profile people willing to act as Assange's bond guarantors, including the British filmmaker Ken Loach and socialite Jemima Khan, the former wife of famed Pakistani cricket player Imran Khan.
Stephens called the outcome "unfortunate" but said Assange would make another bail application.
"This is going to go viral," he said. "Many people believe Mr. Assange to be innocent, myself included. Many people believe the prosecution to be politically motivated."
He expressed confidence that Britain's judicial system was "robust enough" not to be intimidated by political pressure, but declared the same could not be said for Sweden's.
India - Local Council Bans Cell Phones for Unmarried Women
INDIA - LOCAL COUNCIL BANS CELL PHONES FOR UNMARRIED WOMEN
AFP/File ˆ Photo illustration. A local council in northern India has banned unmarried women from carrying mobile ∑
November 24, 2010
NEW DELHI (AFP) ˆ A local council in northern India <http://news.yahoo.com/s/afp/lifestyleindiatelecommarriage##> has banned unmarried women from carrying mobile telephones to halt a series of illicit romances between partners from different castes, media reports said Wednesday.
The Baliyan council in Uttar Pradesh state decided to act after at least 23 young couples ran away and got married over the last year against their parents' wishes.
"The panchayat (assembly) was convinced that the couples planned their elopement over their cell phones," village elder Jatin Raghuvanshi told the Calcutta Telegraph.
The rules of inter-caste marriages <http://news.yahoo.com/s/afp/lifestyleindiatelecommarriage##> are complicated and extremely rigid in many rural communities in India, with some lovers even murdered in "honour killings" by relatives trying to protect their family's reputation.
"All parents were told to ensure their unmarried daughters do not use cell phones. The boys can do so, but only under their parents' monitoring," said Satish Tyagi, a spokesman for the village assembly.
Caste discrimination <http://news.yahoo.com/s/afp/lifestyleindiatelecommarriage##> is banned in India but still pervades many aspects of daily life, especially outside the cities.
Traditional Hindu society breaks down into brahmins (priests and scholars), kshatriya (soldiers), vaishya (merchants) and shudra (labourers). Below the caste system are the Dalits <http://news.yahoo.com/s/afp/lifestyleindiatelecommarriage##> , formerly known as "Untouchables".
Caste categories often determine Indians' life prospects, and conservative families will only marry within their own caste sub-division.
An Insight into BackTrack Linux Penetration Testing Distribution
to the information security field.
www.backtrack-linux.org
VirtualBox 3.2.12 for Linux
VirtualBox 3.2.12 for Linux ¶
Note: The package architecture has to match the Linux kernel architecture, that is, if you are running a 64-bit kernel, install the appropriate AMD64 package (it does not matter if you have an Intel or an AMD CPU). Mixed installations (e.g. Debian/Lenny ships an AMD64 kernel with 32-bit packages) are not supported. To install VirtualBox anyway you need to setup a 64-bit chroot environment.
Please choose the appropriate package for your Linux distribution:
- Ubuntu 10.10 ("Maverick Meerkat") i386 | AMD64
- Ubuntu 10.04 LTS ("Lucid Lynx") i386 | AMD64
- Ubuntu 9.10 ("Karmic Koala") i386 | AMD64
- Ubuntu 9.04 ("Jaunty Jackalope") i386 | AMD64
- Ubuntu 8.04 LTS ("Hardy Heron") i386 | AMD64
- Debian 6.0 ("Squeeze") i386 | AMD64
- Debian 5.0 ("Lenny") i386 | AMD64
- Debian 4.0 ("Etch") i386 | AMD64
- openSUSE 11.3 i386 | AMD64
- openSUSE 11.1 / 11.2 i386 | AMD64
- openSUSE 11.0 i386 | AMD64
- SUSE Linux Enterprise Server 11 (SLES11) i386 | AMD64
- SUSE Linux Enterprise Server 10 (SLES10) i386 | AMD64
- Fedora 14 ("Laughlin") i386 | AMD64
- Fedora 13 ("Goddard") i386 | AMD64
- Fedora 12 ("Constantine") i386 | AMD64
- Fedora 11 ("Leonidas") i386 | AMD64
- Fedora 9 ("Sulphur") / 10 ("Cambridge") i386 | AMD64
- Mandriva 2010.0 / 2010.1 i386 | AMD64
- Mandriva 2009.1 i386 | AMD64
- Red Hat Enterprise Linux 6 ("RHEL6") i386 | AMD64
- Red Hat Enterprise Linux 5 ("RHEL5") / Oracle Enterprise Linux 5 ("OEL5") / CentOS 5 i386 | AMD64
- Red Hat Enterprise Linux 4 ("RHEL4") / Oracle Enterprise Linux 4 ("OEL4") / CentOS 4 i386
- Turbolinux 11 i386 | AMD64
- All distributions i386 | AMD64
You might want to compare the
to verify the integrity of downloaded packages.
Debian-based Linux distributions ¶
Add one of the following lines according to your distribution to your /etc/apt/sources.list:
deb http://download.virtualbox.org/virtualbox/debian maverick non-free deb http://download.virtualbox.org/virtualbox/debian lucid non-free deb http://download.virtualbox.org/virtualbox/debian karmic non-free deb http://download.virtualbox.org/virtualbox/debian jaunty non-free deb http://download.virtualbox.org/virtualbox/debian intrepid non-free deb http://download.virtualbox.org/virtualbox/debian hardy non-free deb http://download.virtualbox.org/virtualbox/debian squeeze non-free deb http://download.virtualbox.org/virtualbox/debian lenny non-free deb http://download.virtualbox.org/virtualbox/debian etch non-free
The Oracle public key for apt-secure can be downloaded here. You can add this key with
sudo apt-key add oracle_vbox.asc
or combine downloading and registering:
wget -q http://download.virtualbox.org/virtualbox/debian/oracle_vbox.asc -O- | sudo apt-key add -
The key fingerprint is
7B0F AB3A 13B9 0743 5925 D9C9 5442 2A4B 98AB 5139 Oracle Corporation (VirtualBox archive signing key) <info@virtualbox.org>
(As of VirtualBox 3.2, the signing key was changed. The old Sun public key for apt-secure can be downloaded here.)
To install VirtualBox, do
sudo apt-get update sudo apt-get install virtualbox-3.2
Replace virtualbox-3.2 by
- virtualbox-3.1 to install VirtualBox 3.1.8
- virtualbox-3.0 to install VirtualBox 3.0.14
- virtualbox-2.2 to install VirtualBox 2.2.4
- virtualbox-2.1 to install VirtualBox 2.1.4
- virtualbox-2.0 to install VirtualBox 2.0.12
- virtualbox to install VirtualBox 1.6.6
Note: Ubuntu/Debian users might want to install the dkms package to ensure that the VirtualBox host kernel modules (vboxdrv, vboxnetflt and vboxnetadp) are properly updated if the linux kernel version changes during the next apt-get upgrade. For Debian it is available in Lenny backports and in the normal repository for Squeeze and later. The dkms package can be installed through the Synaptic Package manager or through the following command:
sudo apt-get install dkms
What to do when experiencing The following signatures were invalid: BADSIG ... when refreshing the packages from the repository?
# sudo -s -H # apt-get clean # rm /var/lib/apt/lists/* # rm /var/lib/apt/lists/partial/* # apt-get clean # apt-get update
RPM-based Linux distributions ¶
Starting with VirtualBox 3.0.12 we provide a yum-style repository for Fedora/RHEL/openSUSE. Note that 3.0.x .rpm packages are named VirtualBox-3.0.x while 3.1.x .rpm packages are named VirtualBox-3.1-3.1.x. This naming scheme allows to use the older 3.0.x packages without changing the repository.
Furthemore, all .rpm packages are signed. The Oracle public key for rpm can be downloaded here. You can add this key (not necessary for yum users, see below!) with
sudo rpm --import oracle_vbox.asc
or combine downloading and registering:
wget -q http://download.virtualbox.org/virtualbox/debian/oracle_vbox.asc -O- | rpm --import -
The key fingerprint is
7B0F AB3A 13B9 0743 5925 D9C9 5442 2A4B 98AB 5139 Oracle Corporation (VirtualBox archive signing key) <info@virtualbox.org>
After importing the public key, the package signature can be checked with
rpm --checksig PACKAGE_NAME
Note that importing the key is not necessary for yum users (Fedora/RHEL/CentOS) when using one of the virtualbox.repo files from below as yum downloads and imports the public key automatically''
The package signature is checked by yum/zypper as well:
- Users of Fedora can add the Fedora repo file to /etc/yum.repos.d/.
- Users of RHEL can add the RHEL repo file to /etc/yum.repos.d/.
- Users of openSUSE can add the proper repo file for 10.3 (VirtualBox 3.0.x only), 11.0, 11.1, 11.2 or 11.3 to /etc/zypp/repos.d/.
Note: Users of Fedora/Mandriva might want to install the dkms package (not available on openSUSE) to ensure that the VirtualBox host kernel modules (vboxdrv, vboxnetflt and vboxnetadp) are properly updated if the linux kernel version changes during the next kernel update.
source: www.virtualbox.org
How To Install Unity In Ubuntu 10.04 Lucid Lynx Netbooks
Application: Ubuntu Netbook Edition 10.10
To install Unity in Ubuntu 10.04, simply follow the following steps:
Open the terminal:sudo apt-add-repository ppa:canonical-dx-team/une
sudo apt-get update
sudo apt-get install unity
Log-off and choose Unity in the GDM sessionsFeatures: Many useful and interesting features. here is a list of what we noticed:
- A launcher and application switcher
- A panel where indicators behave uniformly.
- A view of your installed applications, with Ubuntu Software Center integration.
- A view of your files, with quick access to favorite folders, recent files, downloads, and simple browsing.
- A search field, enabling pervasive use of find-as-you-type search so you can find applications, files, and settings with a few keystrokes.
Tester Note: We do not recommend running Unity on 1GB RAM Netbooks. It will slow things for you. if you find alternatives to make it fast, ignore this note.
According to Mark Shuttleworth, he announced a version of Ubuntu for the dual-boot called Unity and a range of Light versions of Ubuntu, both netbook and desktop, that are optimised for dual-boot scenarios. These "Light" Ubuntu versions are optimized for the web.
The Unity interface will also be available for the Desktop, with a dual-boot for instant web access (known as Ubuntu Netbook Light and Ubuntu Desktop Light). However, Ubuntu Light for the Desktop will only be available for OEM's, and you won't be able to download Ubuntu Light from ubuntu.com.
How to crack Windows 7 password
This video shows how Hiren's Boot CD 12 - Offline NT/2000/XP/VISTA/7 Password changer was used to access Windows 7 SAM System Security and made changes to the existing windows accounts. It will be useful to Admin/Support who are call to a forgotten password scene.
Crack Windows XP password using Hirens Boot CD
Here is a simple video on how it is done.
How to instal windows in VirtualBox
How to install Windows 7
Windows 7 System requirements
1 gigahertz (GHz) or faster 32-bit (x86) or 64-bit (x64) processor.
1 gigabyte (GB) RAM (32-bit) or 2 GB RAM (64-bit)
16 GB available hard disk space (32-bit) or 20 GB (64-bit)
DirectX 9 graphics device with WDDM 1.0 or higher driver.
Ubuntu Unity to dump X for Wayland
Click on the image for high resolution screenshot.
Ubuntu founder Mark Shuttleworth announced on his blog that the Ubuntu distribution will move away from the traditional X.org display environment to Wayland a more modern alternative.
Wayland is a 'display server' for the Linux desktop and an associated protocol. Wayland's main function is compositing:applications render graphics in their own buffers and Wayland composites those buffers into the screen image. This is a simpler and more efficient approach than using a compositing window manager with the X Window System.[1] - Wikipedia
http://www.markshuttleworth.com/archives/551
The next major transition for Unity will be to deliver it on Wayland, the OpenGL-based display management system. We'd like to embrace Wayland early, as much of the work we're doing on uTouch and other input systems will be relevant for Wayland and it's an area we can make a useful contribution to the project.
We're confident we'll be able to retain the ability to run X applications in a compatibility mode, so this is not a transition that needs to reset the world of desktop free software. Nor is it a transition everyone needs to make at the same time: for the same reason we'll keep investing in the 2D experience on Ubuntu despite also believing that Unity, with all its GL dependencies, is the best interface for the desktop. We'll help GNOME and KDE with the transition, there's no reason for them not to be there on day one either.
Timeframes are difficult. I'm sure we could deliver *something* in six months, but I think a year is more realistic for the first images that will be widely useful in our community. I'd love to be proven conservative on that ![]() but I suspect it's more likely to err the other way. It might take four or more years to really move the ecosystem. Progress on Wayland itself is sufficient for me to be confident that no other initiative could outrun it, especially if we deliver things like Unity and uTouch with it. And also if we make an early public statement in support of the project. Which this is!
but I suspect it's more likely to err the other way. It might take four or more years to really move the ecosystem. Progress on Wayland itself is sufficient for me to be confident that no other initiative could outrun it, especially if we deliver things like Unity and uTouch with it. And also if we make an early public statement in support of the project. Which this is!
In coming to this view, several scenarios were considered.
One is the continued improvement of X, which is a more vibrant project these days than it once was. X will be around a long time, hence the importance of our confidence levels on the idea of a compatibility environment. But we don't believe X is setup to deliver the user experience we want, with super-smooth graphics and effects. I understand that it's *possible* to get amazing results with X, but it's extremely hard, and isn't going to get easier. Some of the core goals of X make it harder to achieve these user experiences on X than on native GL, we're choosing to prioritize the quality of experience over those original values, like network transparency.
We considered the Android compositing environment. It's great for Android, but we felt it would be more difficult to bring the whole free software stack along with us if we pursued that direction.
We considered and spoke with several proprietary options, on the basis that they might be persuaded to open source their work for a new push, and we evaluated the cost of building a new display manager, informed by the lessons learned in Wayland. We came to the conclusion that any such effort would only create a hard split in the world which wasn't worth the cost of having done it. There are issues with Wayland, but they seem to be solvable, we'd rather be part of solving them than chasing a better alternative. So Wayland it is.
In general, this will all be fine – actually *great* – for folks who have good open source drivers for their graphics hardware. Wayland depends on things they are all moving to support: kernel modesetting, gem buffers and so on. The requirement of EGL is new but consistent with industry standards from Khronos – both GLES and GL will be supported. We'd like to hear from vendors for whom this would be problematic, but hope it provides yet another (and perhaps definitive) motive to move to open source drivers for all Linux work.